Are you battling a relentless barrage of fraudulent pop-ups on your iPad Air 2, leaving you frustrated and vulnerable? The digital realm is unfortunately rife with deceptive tactics, and these persistent pop-ups are a telltale sign of a potential security threat that demands immediate attention.
The digital landscape, while offering immense opportunities, is unfortunately marred by a persistent threat: fraudulent pop-ups. These unwelcome intrusions, especially when they plague devices like the iPad Air 2, can be incredibly frustrating. You've likely tried the standard remedies disabling Wi-Fi, activating airplane mode yet the pop-ups persist, a clear indication that something more sinister is at play. Recognizing the nature of these threats and knowing how to respond is crucial for protecting your device and your personal information.
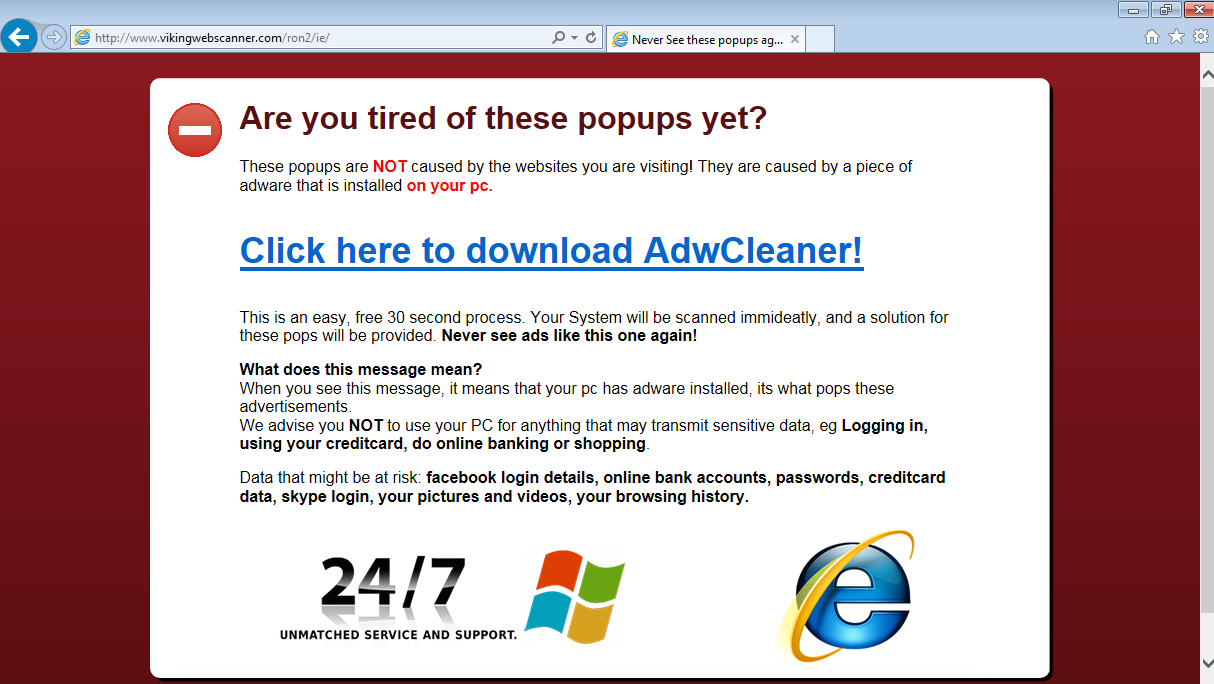
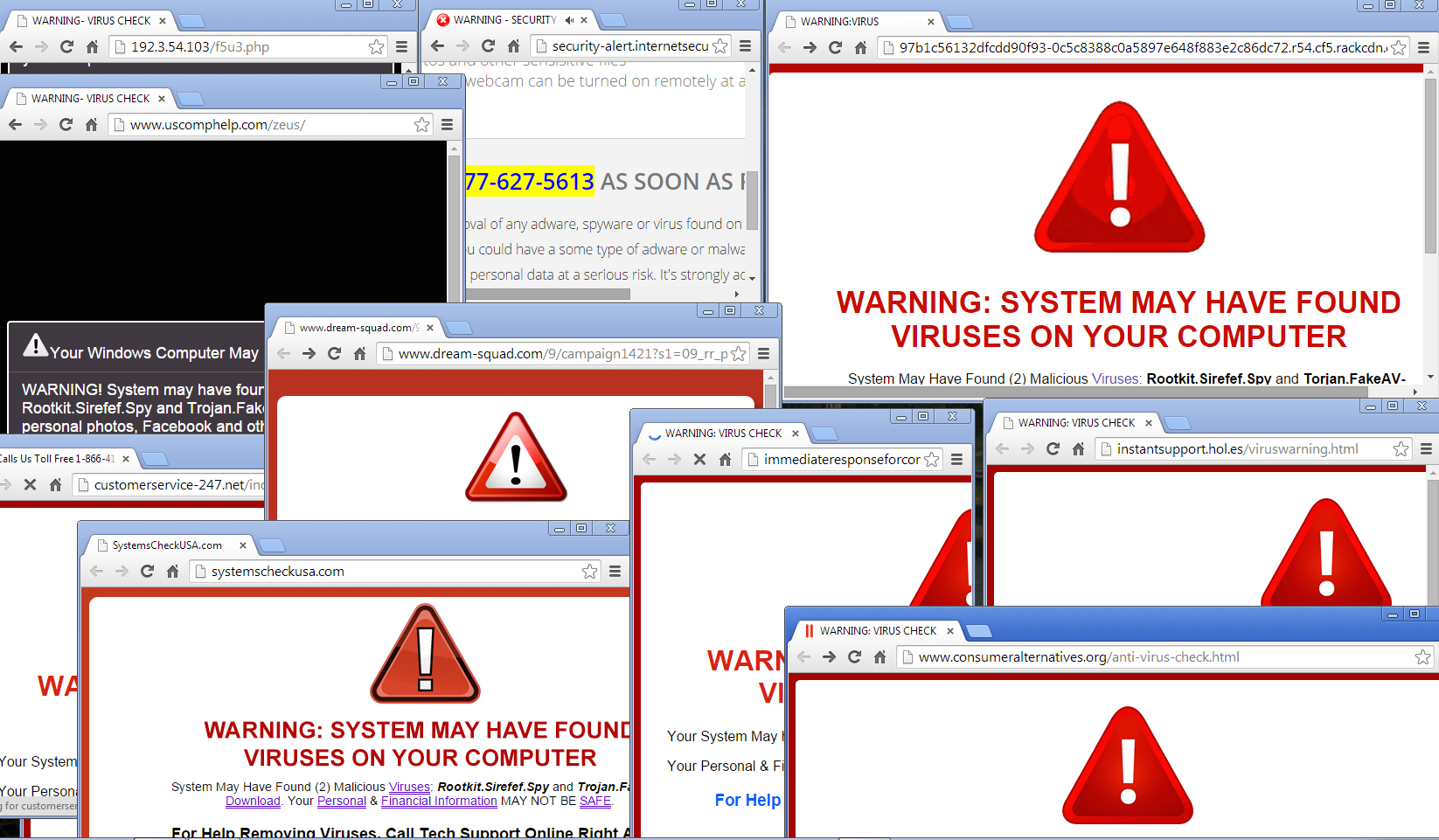
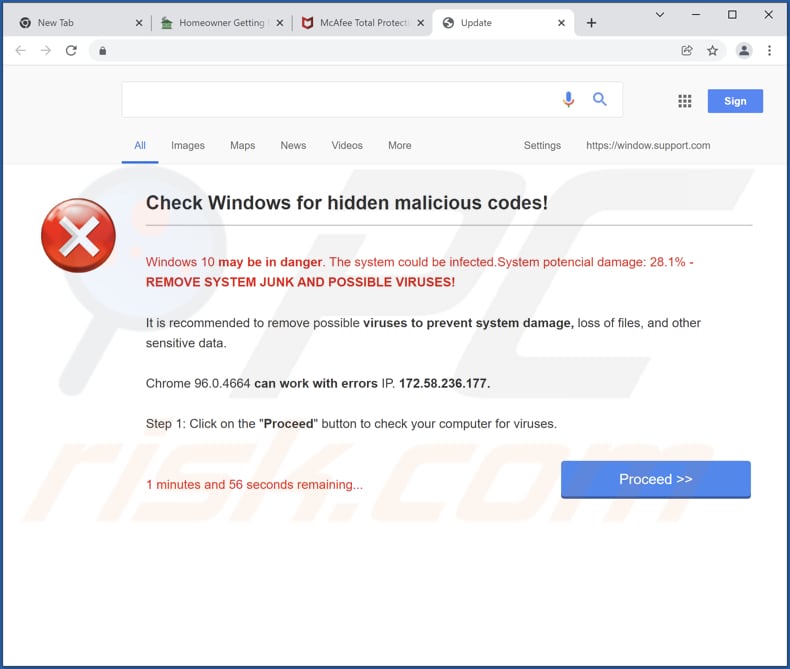
The common targets include fake security alerts. These alerts often mimic legitimate warnings from reputable security companies or operating systems. They are designed to create a sense of urgency and fear, prompting you to take immediate action, often by clicking a link or calling a phone number.
The motives behind these scams are varied but ultimately boil down to financial gain through identity theft, malware installation, and extortion. The scammers are not interested in providing genuine security solutions; they are focused on exploiting your trust and vulnerability.
Heres what you need to know to protect yourself:
- Recognize the Red Flags: Fake security alerts are designed to trick you into action. Be vigilant and look for these key warning signs:
- Urgent Language: Alerts that create a sense of panic or pressure you to act immediately.
- Suspicious Links: Links to unfamiliar websites or those that appear to be misspelled or altered.
- Requests for Personal Information: Alerts that ask for your username, password, credit card details, or other sensitive data.
- Unsolicited Calls: Calls from individuals claiming to be from tech support or security firms.
The techniques employed by scammers are constantly evolving, but some methods are consistently effective. A common tactic involves hacked websites. Cybercriminals exploit vulnerabilities in websites to redirect visitors to scam pages. When you visit a compromised website, you are automatically forwarded to the deceptive site, where the fake security alert is displayed.
Another common tactic is email spoofing. Scammers send emails that appear to be from legitimate companies, such as Microsoft or Apple. These emails may contain links that lead to fake security alerts or malware downloads.
The methods scammers use to gain access to your computer are varied and constantly evolving. They may exploit vulnerabilities in your operating system or software, trick you into downloading malware, or use phishing techniques to steal your login credentials. It is very important to understand how the scammers get access to your devices:
- Malicious Websites: Visiting compromised websites that automatically download malware.
- Phishing: Falling for deceptive emails or messages that trick you into revealing your login information or other personal data.
- Malware: Accidentally downloading and installing malicious software.
- Social Engineering: Being manipulated into providing sensitive information or granting access to your device.
The tactics that scammers use to display fake security alerts on your computer are also diverse and often involve: deceptive alerts. The alerts may appear as pop-up windows, browser notifications, or even full-screen warnings. They may mimic the appearance of legitimate security software or operating system warnings.
Scammers employ multiple tricks to achieve their objectives and here are some examples:
- Pop-up warnings: Deceptive messages are displayed on your screen that look like they come from your security software or operating system.
- Fake virus scans: Simulated scans are conducted and show the presence of malware, even if it doesn't exist.
- Direct download prompts: You are prompted to download a "security tool" that is actually malware.
Should you encounter a fake Microsoft security alert, your immediate response is critical. The most important step is to close the alert immediately without clicking on any links or providing any information. Do not call any phone numbers listed in the alert, as these will connect you directly to the scammers. Consider running a full scan with your installed security software to check for any existing threats.
Similarly, be wary of fake Apple virus warnings, messages, and security alerts. These are crafted to mislead you into calling a number or clicking a link. Just as with Microsoft alerts, do not engage. Close the alert and, if concerned, contact Apple Support directly through their official website. Beware of phone numbers or links provided in the alert. They are designed to compromise you.
Remember, the aim of these scams is not to protect your device. The real objectives are identity theft, malware installation, and extortion. Your vigilance is your strongest defense. Regularly update your security software, keep your operating system and software up-to-date, and be wary of any unsolicited messages or warnings.
If you are unsure about the legitimacy of a security alert, always consult the official website of the company or security provider. Do not rely on the information presented in the alert itself, as this information is often designed to be misleading.
In addition to these steps, consider the following preventive measures to strengthen your online security:
- Install and maintain reliable security software: Use a reputable antivirus and anti-malware program. Keep the software updated.
- Back up your data: Regularly back up your important files to protect against data loss.
- Be cautious of suspicious links and attachments: Never click on links or open attachments from unknown sources.
- Use strong passwords: Create strong, unique passwords for each of your online accounts.
- Enable two-factor authentication: Use two-factor authentication whenever possible to add an extra layer of security.
By understanding the nature of fraudulent pop-ups, recognizing the red flags, and implementing the recommended precautions, you can significantly reduce your risk of falling victim to these scams and protect your iPad Air 2 and other devices from cyber threats.
The digital world offers endless opportunities. But it is important to remember that vigilance, informed action, and consistent security practices remain your best defense against the threats that seek to exploit you. With informed awareness and diligent precautions, you can confidently navigate the online world, free from the fear of these disruptive and potentially harmful pop-ups.